Top Kali linux tools for Penetration testing and hacking
Want to find out about Top Kali Linux Penetration testing and Hacking tools, then here is list of top Kali linux hacking tools used by Cybersecurity Professionals and Ethical Hackers worldwide.
Kali Linux is a Debian-derived Linux distribution that is maintained by Offensive Security. It is geared towards cyber security professionals, penetration testers, and ethical hackers. It’s one of the most popular security distributions in use by Infosec companies and ethical hackers.
Kali Linux includes numerous tools for information gathering, vulnerability analysis, wireless attacks, exploitation tools, forensic tools, sniffing and spoofing, password cracking, reverse engineering, hardware hacking, and much more.
It comes with a lot of these hacking and penetration testing tools preinstalled so that you are ready to start hacking and pen-testing without going through the lengthy process of installing and setting up these tools yourself, saving you a ton of time.
Even if you are not a hacker or a cyber-security professional or just someone who is trying to know more about Kali and its hacking tools or are curious to learn in general then, in this article we are going to discuss top-used Kali Linux tools by cyber security professionals and ethical hackers.
All of these tools come preinstalled with Kali Linux. More detailed documentation about the tools discussed below can be found on the official Kali Tools documentation.
1. Nmap
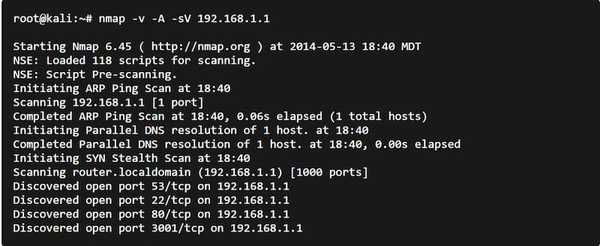
Nmap ("Network Mapper") is a free and open-source (license) utility for network discovery and security auditing.
Nmap uses raw IP packets to get insights about the host, its IP address, OS detection, what services (application name and version) those hosts are offering, what type of packet filters/firewalls are in use, and dozens of other characteristics.
Nmap allows you to gather information about the network, routers, firewalls, and servers. Nmap is cross-platform and is available as an official binary package for Linux, Windows, and Mac OS X.
Checkout Nmap2. Bettercap
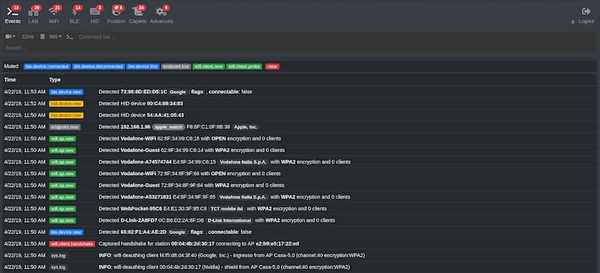
Bettercap is an easy to use, all-in-one solution for performing reconnaissance and attacking WiFi networks, Bluetooth Low Energy devices, wireless HID devices and IPv4/IPv6 networks.
Bettercap is a portable framework written in Go and is famous among security researchers, red teamers and reverse engineers.
Key Features:
- WiFi networks scanning, deauthentication attack, clientless PMKID association attack and automatic WPA/WPA2 client handshakes capture.
- ARP, DNS, DHCPv6 and NDP spoofers for MITM attacks on IPv4 and IPv6 based networks.
- Proxies at packet level, TCP level and HTTP/HTTPS application level.
- An easy to use web user interface.
3. BurpSuite
BurpSuite is one of the most powerful integrated platform for performing security testing of web applications.
BurpSuite allows us to make changes to those requests made by web applications which is useful for finding vulnerablities and later can be used to design exploits.
It has various ethical hacking tools inbuilt that work seamlessly together to support the entire penetration testing process.
root@kali:~# burpsuite --helpUsage:--help Print this message--version Print version details--disable-extensions Prevent loading of extensions on startup--diagnostics Print diagnostic information--use-defaults Start with default settings--collaborator-server Run in Collaborator server mode
4. WireShark
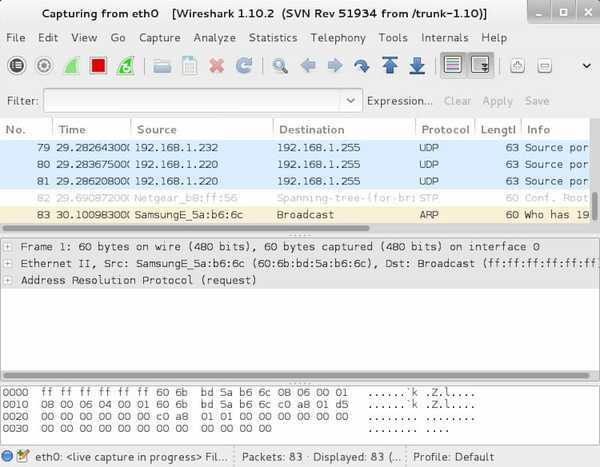
Wireshark is most widely-used network protocol analyzer. It is mainly used for network sniffing. Wireshark allows you to ispect each individual packets being transmitted over the network.
These packets may have information like the source IP and the destination IP, the protocol used, and the information being carried by packets.
Key Features:
- Deep inspection of hundreds of protocols.
- Multi-platform: Runs on Windows, Linux, macOS, Solaris, FreeBSD, NetBSD, and many others.
- Rich VoIP analysis.
- Read/write many different capture file formats.
root@kali:~# tshark -hTShark (Wireshark) 3.4.8 (Git v3.4.8 packaged as 3.4.8-1)Dump and analyze network traffic.See https://www.wireshark.org for more information.Usage: tshark [options] ...
5. Aircrack-ng
Aircrack-ng is one of the best Kali Linux ethical hacking tools wireless networks. It consists of a network packet analyzer, a WEP network cracker, and WPA / WPA2-PSK along with another set of wireless auditing tools.
Aircrack-ng captures wifi handshake packets and then using its built in hashing tools it can decrypt the hash to get the password.
It works primarily on Linux but also Windows, macOS, FreeBSD, OpenBSD, NetBSD, as well as Solaris and even eComStation 2.
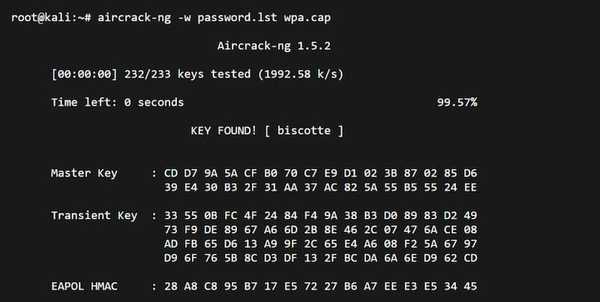
Usage Example:
- -w : Specify wordlist to use
- wpa.cap : specify the pathlist of the capture file containing hashes
6. John the Ripper
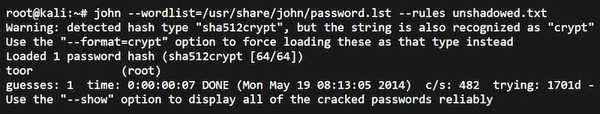
An Open Source password security auditing and password recovery tool. It is multi-platform and works on Unix, Linux, Windows and MacOS.
It is used by cybersecurity professionals to test the encryptions like SHA-1, SHA-256, DES and many others.
John the Ripper jumbo supports hundreds of hash and cipher types, including user passwords of Unix flavors (Linux, BSD, Solaris, AIX, QNX, etc.), macOS, Windows, "web apps" (e.g., WordPress), encrypted private keys (SSH, GnuPG, cryptocurrency wallets, etc.), filesystems and disks (macOS .dmg files and "sparse bundles", Windows BitLocker, etc.), archives (ZIP, RAR, 7z), and document files (PDF, Microsoft Office's, etc.)
Checkout John the Ripper7. Metasploit-Framework
Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. It is one of the world’s most used penetration testing frameworks.
It is written in Ruby and is developed and maintained by Rapid7 LLC. It is cross-platform and works on Linux, macOS and Windows. With Metasploit-Framework you can create exploits for target devices by exploiting the security flaws and gain access of the target system.
You can learn more about the Metasploit-framework by joining this course Metasploit Unleashed, a free online course created by Offensive Security.
Checkout Metasploit-Framework8. Social Engineering Toolkit
The Social-Engineer Toolkit (SET) is an open-source Python-driven tool aimed at penetration testing around Social-Engineering.
SET contains huge list of tools using which you can launch attacks like Wifi AP-based attacks, phishing attacks, deploy payloads, SMS and Email attacks and many more.
Checkout Social Engineering Toolkit9. sqlmap
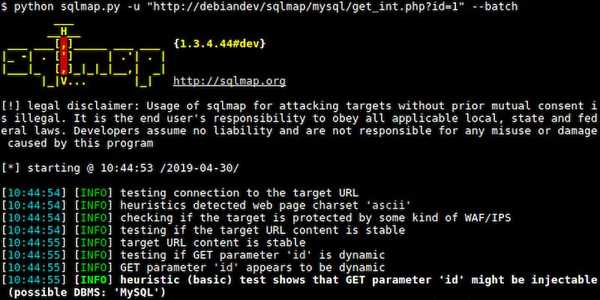
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers.
sqlmap allows you to perfrom database fingerprinting, and also allows you to access the underlying file system and executing commands on the operating system via out-of-band connections.
Key Features:
- Full support for six SQL injection techniques: boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries and out-of-band.
- Support to search for specific database names, specific tables across all databases or specific columns across all databases' tables.
- Download and upload any file from the database server underlying file system.
10. Hydra
Hydra is used to brute-force username and password to different services such as ftp, ssh, telnet, MS-SQL, etc.
It is very fast and flexible, and supports: Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
Checkout Hydra11. Medusa
Medusa is another popular login brute-forcer, just like Hydra. Medusa is speedy, allows parallel execution, and modular.
Key Features:
- Thread-based parallel testing.
- Multiple protocols supported. Many services are currently supported (e.g. SMB, HTTP, POP3, MS-SQL, SSHv2, among others).
- Modular design meaning no modifications are necessary to the core application in order to extend the supported list of services for brute-forcing.
12. Netcat
Netcat is a simple utility tools widely used for administering and debugging networks. Using netcat you can read and write data across network connections, using the TCP or UDP protocols.
Netcat is intended to be a reliable back-end tool which can be used directly or easily driven by other programs and scripts.
Checkout Netcat13. Autopsy
Autopsy is a digital forensics tool used by law enforcement, military, and corporate examiners to investigate what happened on a computer.
Autopsy can help you recover deleted documents, extract history, bookmarks, and cookies from Firefox, Chrome, and IE and even recover files from unallocated spaces.
Key Features:
- Timeline Analysis: Displays system events in a graphical interface to help identify activity.
- Web Artifacts: Extracts web activity from common browsers to help identify user activity.
- Robust File System Analysis: Support for common file systems, including NTFS, FAT12/FAT16/FAT32/ExFAT, HFS+, ISO9660 (CD-ROM), Ext2/Ext3/Ext4, Yaffs2, and UFS from The Sleuth Kit.
- Android Support: Extracts data from SMS, call logs, contacts, Tango, Words with Friends, and more.
- EXIF: Extracts geo location and camera information from JPEG files.
14. Crunch
Crunch is a wordlist generator where you can specify a standard character set or a character set you specify. crunch can generate all possible combinations and permutations.
Key Features:
- Generates wordlists in both combination and permutation ways.
- Pattern now supports upper and lower case characters separately.
- Unicode Support.
15. WPScan

WPScan is a command line tool used for testing the security of any WordPress webiste and applications. Using WPScan bloggers and security professionals can test the security of their WordPress website.
WPScan check for vulnerablities in themes and plugins installed, publically accessible wp-config.php files, users with weak passwords, any database dumps that may be publically available and many more. For this purpose WPScan CLI tool uses database of 23,851 WordPress vulnerabilities.
Checkout WPScan16. Hashcat
Hashcat is one of the world’s fastest and most advanced password recovery tool. It is cross-platform and supports popular hashing algorithms like LM hashes, MD4, MD5, SHA-family and Unix Crypt as well as algorithms used in MySQL and Cisco PIX. Hashcat has two versions:
- hashcat - CPU based password recovery tool and
- oclHashcat/cudaHashcat - GPU-accelerated tool (OpenCL or CUDA). With the release of hashcat v3.00, the GPU and CPU tools were merged into a single tool called hashcat.
Hashcat offers multiple attack modes. These modes are:
- Brute-force attack
- Combinator attack
- Dictionary attack
- Fingerprint attack
- Hybrid attack
- Mask attack
- Permutation attack
- Rule-based attack
- Table-Lookup attack (CPU only)
- Toggle-Case attack
- PRINCE attack
17. Nikto
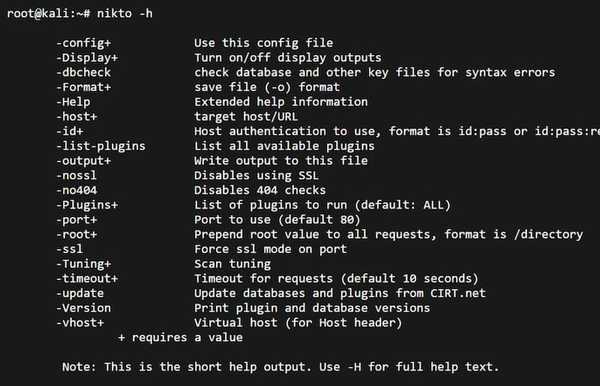
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items.
It scans for over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers.
Some of the key things Nikto checks are:
- Server and software misconfigurations
- Default files and programs
- Insecure files and programs
- Outdated servers and programs
- Pointers to lead a human tester to better manual testing
18. Dirbuster
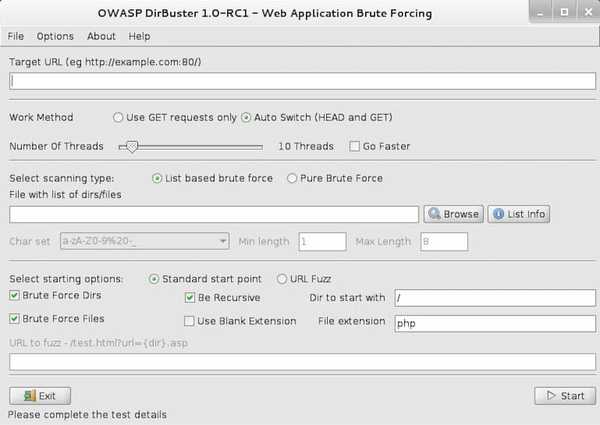
DirBuster is a multi threaded java application designed to brute force directories and files names on web/application servers.
DirBuster comes a total of 9 different lists generated from scratch, by crawling the Internet and collecting the directory and files that are actually used by developers.
DirBuster attempts to find unlinked pages and applications (that shouldn't be public) hidden within a webserver. Dirbuster can help you find these vulerabilities and help make your web/application servers more secure.
DirBuster also has the option to perform a pure brute force, which leaves the hidden directories and files nowhere to hide.
root@kali:~# dirbuster -hDirBuster - 1.0-RC1Usage: java -jar DirBuster-1.0-RC1 -u <URL http://example.com/> [Options]
19. BeEF
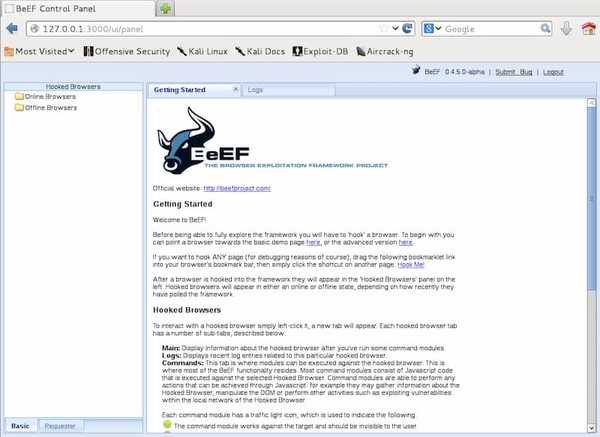
BeEF is a penetration testing tool that focuses on the web browser. BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors.
BeEF focuses on leveraging browser vulnerabilities to assess the security posture of a target. The framework allows the penetration tester to select specific modules (in real-time) to target each browser, and therefore each context.
root@kali:~# beef-xss[*] Please wait for the BeEF service to start.[*][*] You might need to refresh your browser once it opens.[*][*] Web UI: http://127.0.0.1:3000/ui/panel[*] Hook: <script src="http://<IP>:3000/hook.js"></script>[*] Example: <script src="http://127.0.0.1:3000/hook.js"></script>
20. Apktool
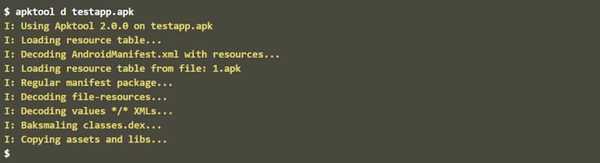
One of the most popular tool for reverse engineering Android apps. Apktool decode apk resources to nearly original form and rebuild them after making some modifications.
It is NOT intended for piracy and other non-legal uses. It could be used for localizing, adding some features or support for custom platforms, analyzing applications and much more.
Key Features:
- Disassembling resources to nearly original form (including resources.arsc, classes.dex, 9.png. and XMLs)
- Rebuilding decoded resources back to binary APK/JAR
- Organizing and handling APKs that depend on framework resources
Final Words: Kali Linux most widely used tools for Penetration testing and Hacking
Above tools were some of the top tools used by Cybersecurity Professionals and Hackers. There are lot of tools that come bundled with Kali Linux.
To find more about these tools and all the tools that come bundled with Kali Linux, you can visit the official Kali Tools documentation.
Read: 41 Best Hacking Apps For Android Rooted & Non Rooted 2021
So, that's all. Hope you like our list of top Kali Linux Penetration testing and hacking tools.
If you think that there is some tool that we forgot to mention here, then feel free to drop your suggestions in the comment section below.
